Say what?
In my original post Encryption - breaking the myth, I endeavored to use "my flavor of irony" sprinkled with a touch of sarcasm, to spark some thought and debate.Then my lovely wife and I played with a visual presentation "Encryption - shatter the myth", and still I muse about "what are these big companies thinking?".
I imagine... they are imagining... that we can hope no one will every breach a server again. Let's make it terribly difficult to be online... so what if our employees need to use, "difficult to use" corporate laptops to "occasionally" check their email. And yet, the breaches continue.
This led to the second blog post "Encryption - breaking the myth series - part 2".
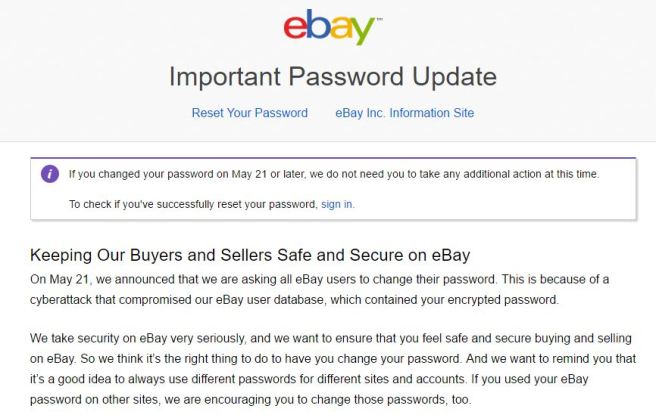
 |
| I've stolen my copy, just have to break the encryption now |
One of my favorite blogs (very subjective here) is my 3'rd blog about my prime number generator. This blog references what I like to call an "Organic Sieve". Maybe it isn't perfectly clear, but lets get to the bottom line: with organic sieves, one can readily "look up" any prime number - am I the only one the realizes what this says about encryption?
Game Of... Numbers
As I continue to blog and dialog with "people", I occasionally find inspiration in the strangest ways and times. Someone I consider to be quite brilliant with technology contrasted "prime number" based encryption with "other types". Ya, how about "strong passwords"?Just for fun, lets consider a strong password that uses 10 digits, each of which might have 72 different values (26 lower case, 26 upper case, 10 digits and some special characters). How many possible combinations are involved?
Yes, that is a big number, and that is why strong passwords are important (being force fed I suppose). That is why we often here statistics like, this strong password (above) is more than 12 billion times stronger than a password that uses 6 lower case letters.Lets add one more perspective here, namely, one could argue that this "strong password" is on par with a 63 bit prime number used to encrypt data. Today's standards (without getting too bogged down in details about symmetric or asymmetric algorithms) are well beyond 256 bits.
Simplicity is the ideal lens for capturing 'the complex'
I apologize for the over simplification, its just that I do like "simple", and think fondly of the KISS rule/acronym. The simple truth is that "encryption isn't good enough":
Article - 2016 - hacker & bank (actually reported)
Article - 2016 - University employees vulnerable - tax data breach
Article - 2015 - Lloyd's CEO on the cost of cyber attachs
Article - 2015 - forbes.com - average costs
Article - 2014 - washington post - cost of cyber crimes
bankrate.com: 11 data breaches that stung US consumers
2014 - data breaches by industry